1. Secure Private Cloud
All the IREX production deployments are hosted in a Secure Private Cloud. Unlike most cloud video surveillance systems that run in public clouds, IREX isolates data physically from other enterprise users and other applications. If a super admin account is compromised, the exposed data will be localized in the Secure Private Cloud. Of course, IREX can also operate in a private network (e.g. in an airport) without any connection to the Internet or other public networks.
2. Web Application Firewall
IREX is bundled with a Multilayer Web Application Firewall (WAF), Intrusion Detection System (IDS), Internet Protection System (IPS), and Network Filter. These powerful cybersecurity tools enable the proactive defense against known and unknown cybersecurity attacks. IREX conducts regular penetration tests for each major release per OWASP Testing Guide and other frameworks.
3. Dynamic Keys in the IREX API
IREX uses JSON Web Tokens (JWT) with asymmetric signatures for all the platform microservices, clients, and third-party software connecting to the IREX API. The signature keys are randomly generated and updated on regular basis. So neither software developers nor system installers can use re-use API keys to bypass full user authentication.
4. End-to-End Encryption
As standard, IREX uses HTTPS / TLS 1.3 to encrypt all traffic from its edge devices to the Secure Private Cloud and further to clients. Outside private networks, IREX uses VPN to encrypt RTSP streams from standard IP cameras. IREX sends real-time alerts using its secure messenger hosed in the Secure Private Cloud.
5. Advanced Security Policies
IREX has developed a multi-organizational access control system including hierarchical user groups, comprehensive user roles, and resource groups to manage cameras, IoTs, building plans, people, and vehicle databases. This access control system ensures that users can see only designated real-time alerts and search results.
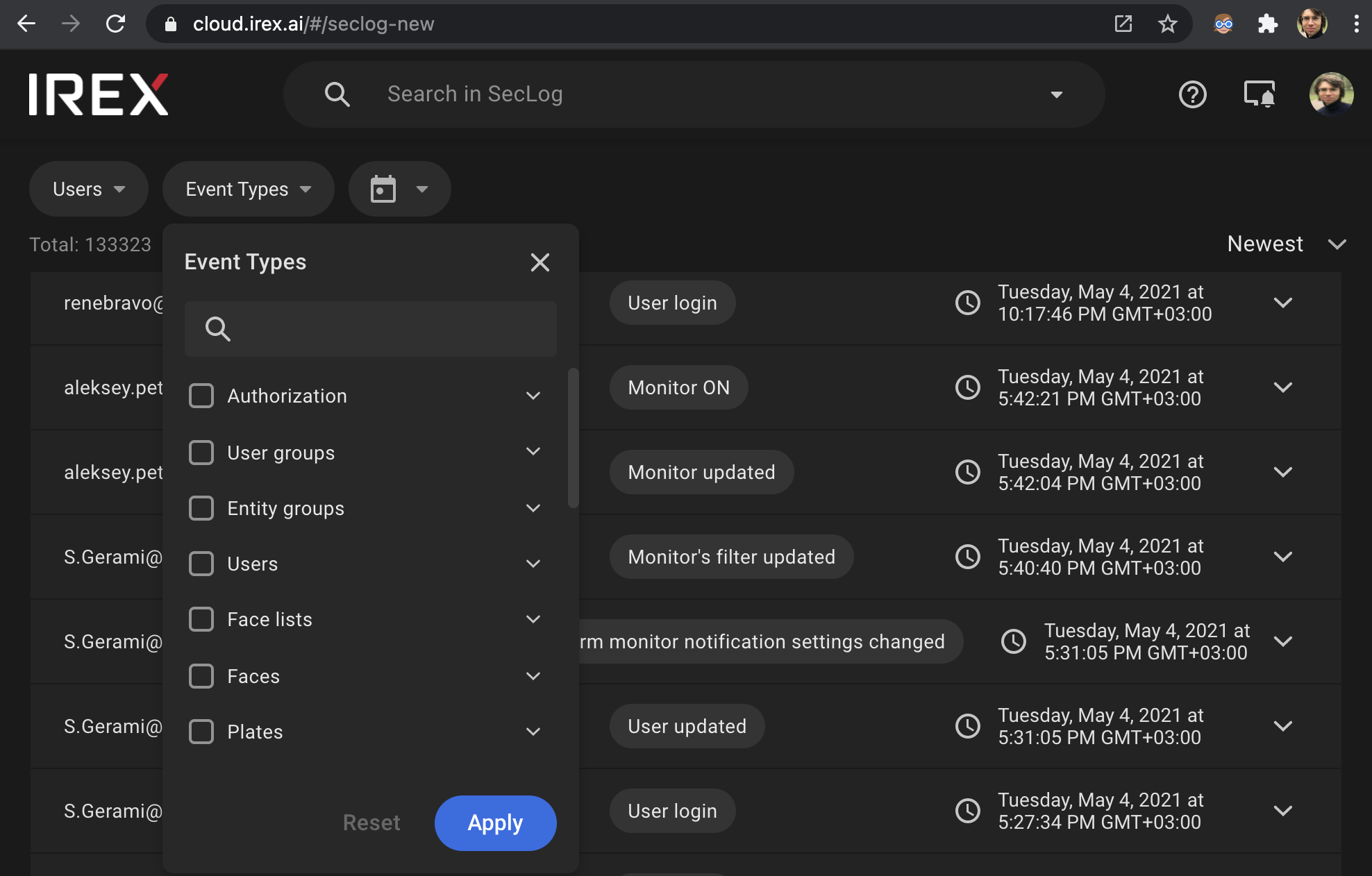
6. Detailed Logging
IREX authenticates all users and records their activities, for example, platform sign-in, facial search, video export, and permission changes. As shown on the screenshot, the log is searchable by user name, event type, and period.
Learn More
IREX Knowledge Database
IREX Smart City Platform Datasheet